A few weeks ago, WPTavern highlighted the recent spike in payment fraud via Stripe on WooCommerce websites. While this issue itself is not new, this post was triggered by a discussion on the Advanced WordPress Facebook Group, by several developers who noticed that their clients’ websites were affected by similar incidents.
And they are not alone.
According to data analyzed by Statista, e-commerce losses due to online payment fraud globally doubled from 20 US billion dollars in 2021 to 41 US billion dollars in 2022. Based on these trends, current projections estimate the number as a whopping 48 billion US dollars in 2023.
Understanding Payment Fraud
Simply put, ‘fraud’ implies stealing what doesn’t belong to you, however, online payment fraud is anything but simple.
What is Payment Fraud?
When a payment is done via an unauthorized transaction i.e. without the approval of the owner of the card or bank account, it is known as payment fraud.
Common Types of Payment Fraud
There are various types of payment frauds that are so smoothly executed that it takes a while for the victims to even realize that they have been tricked.
Card Testing
A fraudster with stolen debit or credit card details makes a few small purchases to confirm that the card details are valid. This is usually known as card testing or card cracking.
Fraudsters often look for websites that allow you to pay any amount (pay-what-you-want) or non-profit websites that accept small amounts as a donation. Else, they identify any random unsuspecting merchant’s website and purchase cheap items to confirm that the stolen card is still active.
To add to this mess, if the fraudster is technically skilled enough to use automated scripts or bots for this, it can lead to a huge number of such transactions in a very short period. More often than not, it is already too late by the time the affected merchant and the actual card owner notice these abnormal transactions and try to stop them.
Triangulation Fraud
This type of fraud can be a complete nightmare, because it is really hard to trace this chain. This is how it usually goes:
A fraudster sets a sham storefront on a marketplace (e.g. e-Bay or Amazon) complete with products.
A genuine customer visits the fraudster’s store and buys a product.
The fraudster then uses a stolen credit card and places an order for that product with a legitimate merchant, with the customer’s shipping address.
Now, the customer does not notice anything abnormal, because she receives exactly what she ordered, using her genuine card details.
When the owner of the stolen card sees the charge on her bill and raises a payment dispute, it is the unsuspecting merchant who has to pay the penalty for the chargeback. With the goods already delivered to someone who had actually paid for the product (albeit, to the fraudster), the merchant has no way of recovering the delivered item or the payment he is owed for it. Plus he ends up paying the penalty fee for the chargeback too.
If the genuine merchant doesn’t up his game and prevent such fraudulent transactions, the losses can mount pretty quickly.
Friendly Fraud
Friendly fraud (also known as a false chargeback) is when a customer buys something using their own valid card from an online retailer but later raises a chargeback with their bank, demanding a refund. This could either be due to buyer’s remorse or a hesitation to contact the merchant and resolve it amicably.
Alternative Refunds
This is when a trickster pays a website (usually a non-profit or a website that accepts pay-what-you-want donations) a large amount, using a stolen card. They then contact the website and claim to have transferred more than what they intended to, requesting a partial refund to an alternative card (his own), again falsely claiming that the card used for the original payment has expired.
Simple Actions to Prevent Hacking and Payment Fraud
To be fair, payment gateway processors do try their best to keep out malicious actors, but that is simply not enough.
In fact, Stripe published a note detailing its response to this recent surge in card testing attacks. While that may have helped to reduce fraud, it is still only a small dent, when you consider the scale of such fraudulent attempts that are successful.
So it is best for you to take the responsibility of keeping your WordPress website safe and do all you possibly can.
Here are 5 simple ways to do so!
1. Enforce a Strong Login Process
A website can only be as secure as its weakest password. Enforcing strong passwords is the very least you can do to prevent hackers from getting access to your website. However, if the password is too complex for humans to remember, then they might get lazy and write it down in an unsecure place. Or if it is easy enough for them to remember, chances are, it is easy to be hacked as well.
Instead of relying only on a strong password, it is highly recommended that you opt for an added layer of security, by adding one more step to the login process. Some of the ways to do that –
2. Monitor Payments Regularly
Watch out for any unusual customer patterns, odd email ids, billing address and IP address location mismatches etc. You could do this manually or use a WooCommerce payment plugin such as the ones listed below.
Here are some WooCommerce WordPress Plugins specifically designed for fraud prevention
SyncTrack Auto Add Paypal
![]()
This is a relatively lesser known free plugin, which was released in 2022 May. What it aims to do is brilliant – it integrates with Paypal and passes on payment tracking information, so that you are protected from disputes and chargebacks related to fraudulent orders.
However, this plugin hasn’t been updated since its release and tested with recent WordPress versions though, so it should be used with caution.
WooCommerce Eye4Fraud

It literally guarantees chargeback protection by promising to fully reimburse you, if a customer raises a chargeback successfully on an Eye4Fraud approved account. Doesn’t get any better than this, I guess.
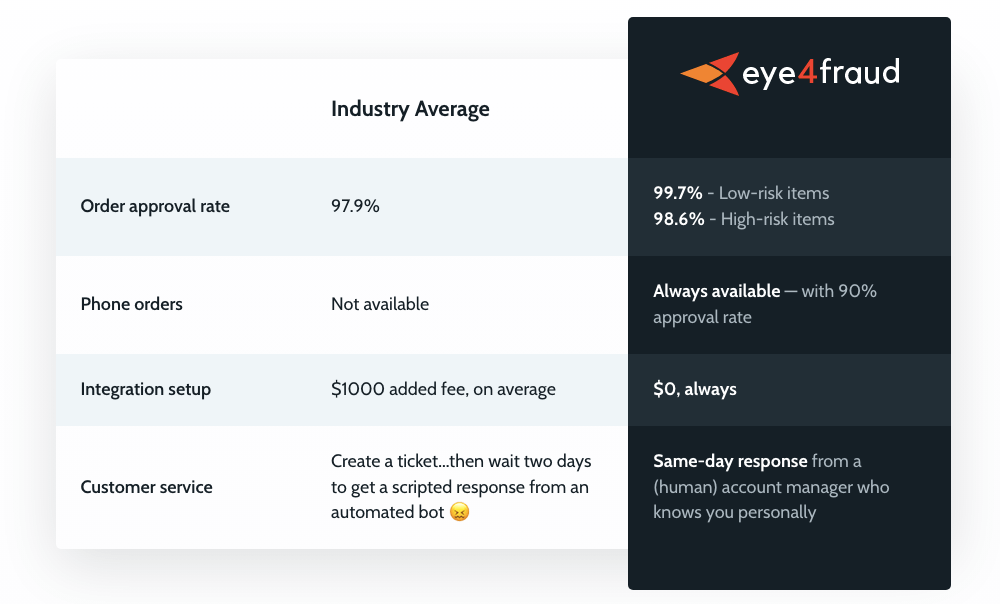
You will need to get an Eye4Fraud account for this to work though and they charge a percentage of your order amount as commission. There’s no pricing information on their website, you can reach out to them for a personalized quote.
YITH WooCommerce Anti-Fraud
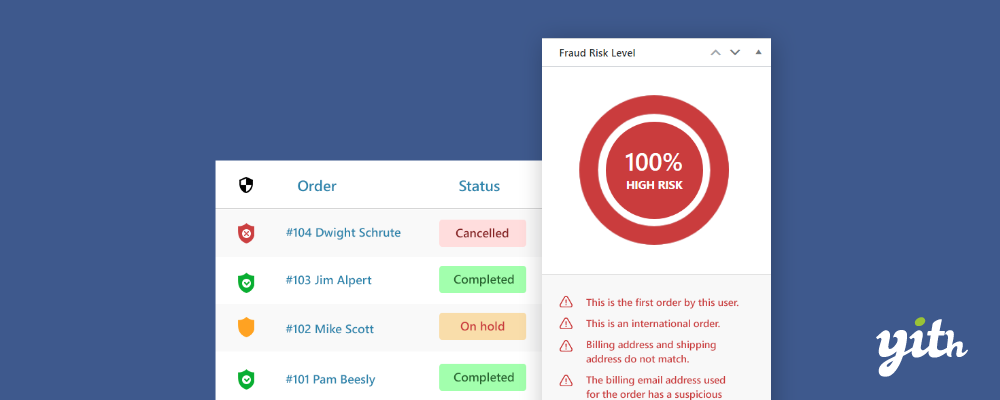
This plugin automatically detects suspicious behavior during the payment process and block orders. For example, any mismatches in parameters such as IP address, geographical location etc.
It also allows you to configure rules for blocking orders based on conditions such as risk threshold, emails from suspicious domains, order amounts that are unusually high (you can specify the amount) and more.
Woocommerce Anti-Fraud by OPMC
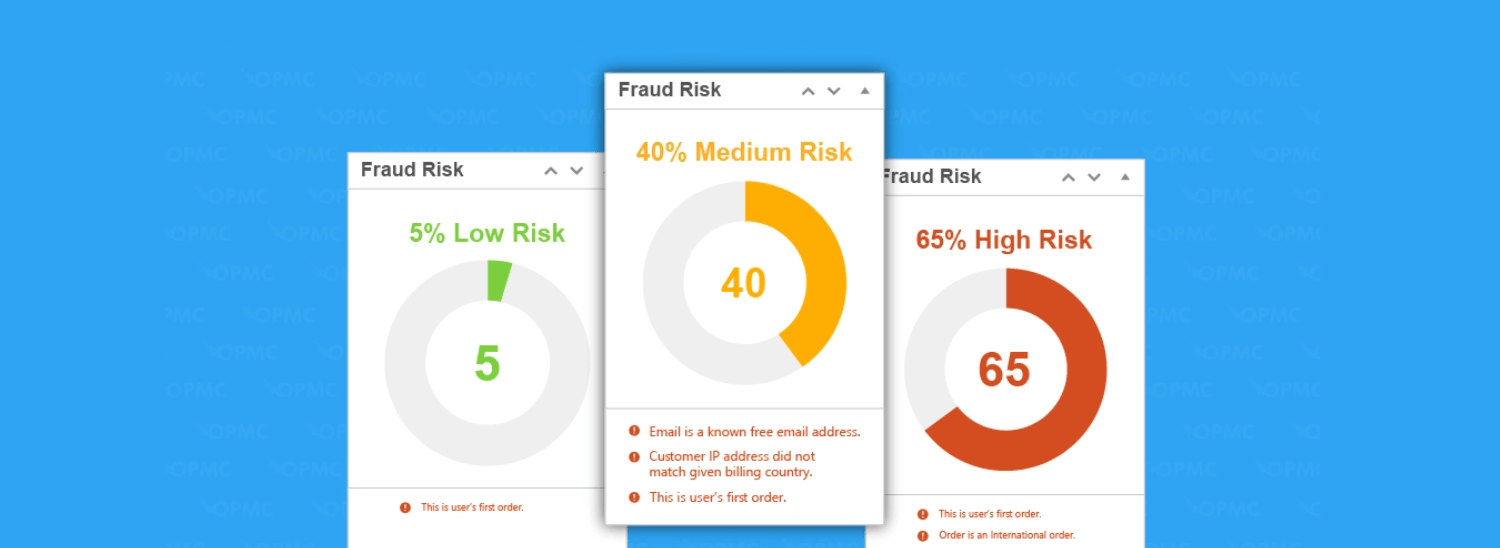
This popular anti-fraud WordPress plugin allows you to set up various rules and alerts based on your expected customer behavior. Any orders that do not conform to this are highlighted, so that you can then look into them more closely.
This plugin also:
Assesses risk associated with each payment and alerts you to high risk payments
Provides protection against velocity attacks using reCAPTCHA
Integrates with QuickEmailVerification to validate email addresses
3. Disable Guest Orders (without Customer Registrations)
Consider forcing users to register on your website before placing an order. You could also add an extra check by forcing new users to validate their email address or by adding a captcha on the registration form (or both).
And if you haven’t, consider adding a captcha to your checkout page as well. Though that might annoy your real customers who want a quick and smooth check out experience it might still be worthwhile.
However, this could help reduce the chances of card testing attacks where multiple orders for small amounts are placed using random non-existent mail ids, by bots.
4. Enable Rate Limiting
The WooCommerce Anti-fraud plugin by YITH allows you to control the number of orders per user within a specified time period. This prevents fraudsters from placing a large number of orders automatically using the same customer id. Not that this prevents it completely of course, but every little helps.
5. Leverage What You Already Have
You should try your best to take advantage of whatever resources you might be using already e.g. your hosting, Cloudflare (or similar security providers).
For example:
You can enable Cloudflare’s Bot Fight mode so that whenever typical bot traffic patterns are noticed, those get blocked by Cloudflare.
Check with your hosting provider as well if they provide any tools or firewalls that might help you handle such attempts.
Also, if you are already using the WooCommerce Payments plugin, it highlights the risk level assessed for each transaction, as ‘Normal’ or ‘Elevated’ – this is based on its integration with Stripe’s RADAR fraud prevention tool.
While you should definitely use whatever means possible to prevent fraud, it is possible that you might still see some fraudulent orders getting through.
The best way to keep damages to a minimum is to stay alert and react quickly to any abnormal buying patterns on your website.
If you see multiple transactions for small amounts in quick succession, you should check the details and immediately block them until you investigate the transactions.
Stay alert, stay safe!

